Adversarial Surveillance Is Conducted to Gather Information in Order to
As Senator Diane. 5 The majority of SVR case officers operate under diplomatic cover from Russian embassies and consulates.

Pdf What S New About The New Surveillance Classifying For Change And Continuity
Executive Order 12333 has not been seriously challenged in courts yet.

. Its a program that from what we know so far is renewed every 90 days. Second when an aggrieved person against whom electronic surveillance evidence has or will be used files a motion to suppress the evidence. Specific intelligence disciplines include but.
And the data collected by the NSA and FBI under those applications often remains secret even when it or information derived from it is used in criminal proceedings. The order is one piece of evidence for a surveillance program that seems to have been ongoing since 2006. Governments gather far too much information about us and in dangerously intrusive ways.
FISA provides special procedures for use when the Government wishes to conduct foreign intelligence surveillance. But as we have. Critics are worried by traditions of oversurveil-lance.
Adversary uses commercial or free software to scan organizational perimeters to obtain a better understanding of the information technology infrastructure and improve the ability to launch successful attacks. Adversarial surveillance is conducted to gather critical information about individualsorganizationsbusinesses and infrastructure in order to commit an act of terrorism or other crime. Perform network sniffing of exposed networks.
Gathering Information 63 These abuses are well documented and the political heirs to their victims have long memories. Accordingly intelligence programs that collect information overseas are governed by the Constitution and executive order. They can be used to gather information to.
Eddington is a senior fellow in homeland security and civil liberties at the Cato Institute. Adversarial surveillance is distinguished by its purpose - to gather information in preparation for an action that is aggressive or criminal in nature. These actions include domestic and international terrorism crimes against individuals espionage theft stalking and.
Its a very broad executive order having to do with intelligence gathering for national security purposes. Not including activities conducted by security investigative law enforcement or other personnel in the normal course of their duties. First when the government provides notice of its intent to use or disclose electronic surveillance evidence against an aggrieved person.
The SVR concentrates on collecting political economic scientific and technical information and relies on HUMINT SIGINT and open source analysis for producing intelligence. Adversarial surveillance is conducted to gather information about individuals organizations businesses and infrastructure in order to commit an act of terrorism or other crime. Air Force surveillance and reconnaissance assets are not inherently strategic operational or tactical in nature.
The interpretation of Executive Order 12333 is of some concern. Perform reconnaissance and gather information. Why the FISA Court Needs to Change.
A Libertarian Vision for Intelligence and Surveillance. For example standard search warrants are used to gather evidence for later prosecutions that are by default public. Defenders of surveillance are worried about the errors attending undersurveillance.
The focus of ISR is on answering a commanders information needs such as identifying and locating adversary activity and intentions within a given battlespace. Executive Order on Protecting Americans Sensitive Data from Foreign. This is generally true regardless of the purpose of the surveillance.
By the authority vested in me as President by the Constitution and the. When conducted abroad against foreigners surveillance falls under the Presidents constitutional authority as Commander-in-Chief. Thats trying to challenge national surveillance law is tricky in court.
Post-911 hindsight lends some support to the advocates of wide sur-. Relevant here FISA provides a procedure under which a trial-level court or other authority may consider the legality of electronic surveillance conducted under FISA and order specified forms of relief. This course will provide you with the information you need to detect adversarial surveillance and to report it.
June 09 2021 Presidential Actions. The court must rely on one-sided information from the government and has to trust that that information is complete. Capabilities conducted through the use of computer networks to gather data from target or adversary automated information systems or net-works11 More explicitly CNE is usually performed through network tools that penetrate adversary systems.
Perform perimeter network reconnaissancescanning. Or third when a motion is. Although surveillance conducted for run-of-the-mill law enforcement is often shadowy the FISA process is far more shielded from public view.
The procedure is available only in three circumstances. Communications acoustics etc collect analyze and share data information and intelligence across multiple warfighting domains. But intelligence services can be more liberty and privacy respecting.
The court finds however that an accurate determination of the legality of the surveillance is best made in this case as part of an adversarial proceeding Fisa surveillance is supposed to occur.
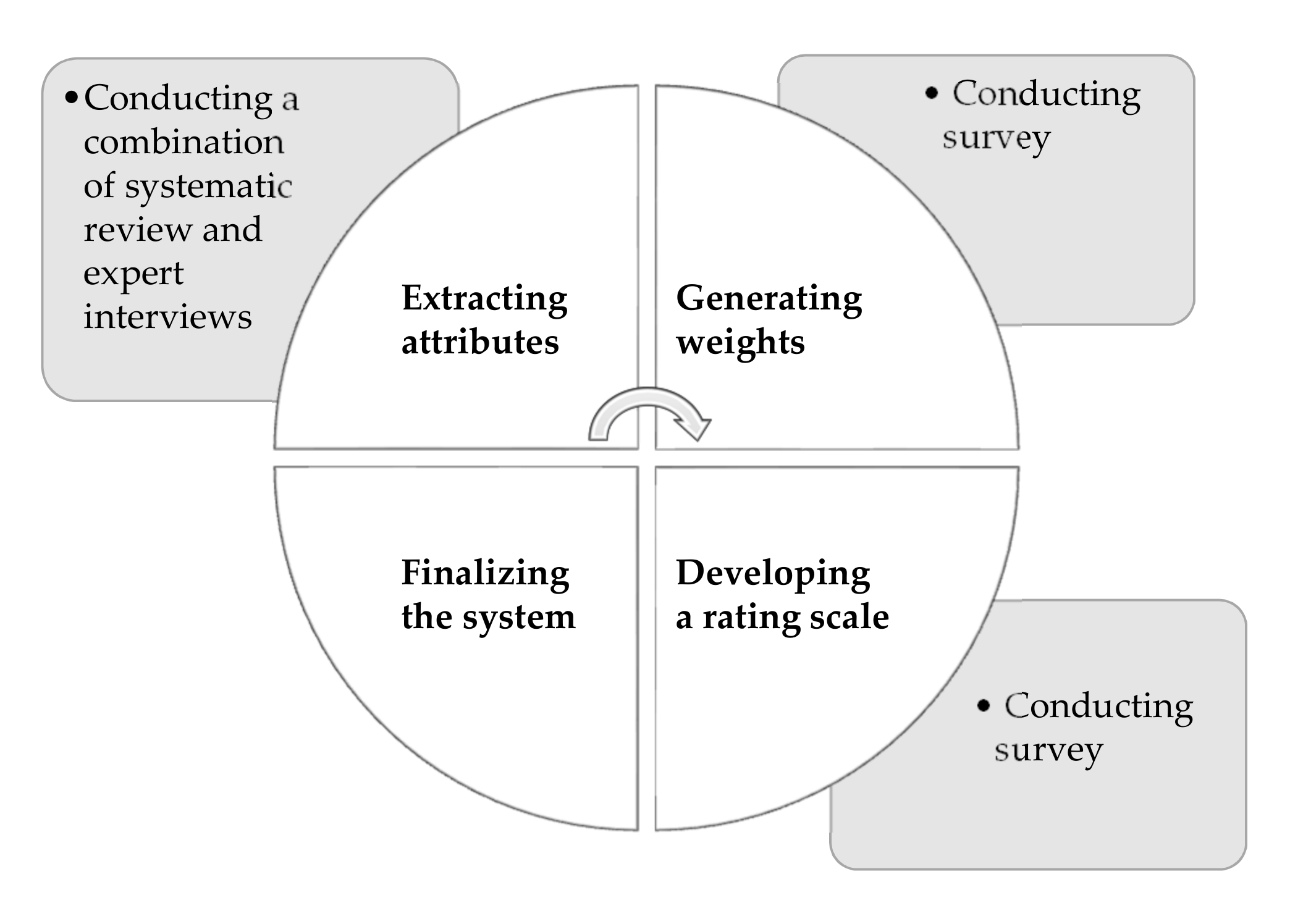
Symmetry Free Full Text Controlling Safety Of Artificial Intelligence Based Systems In Healthcare Html
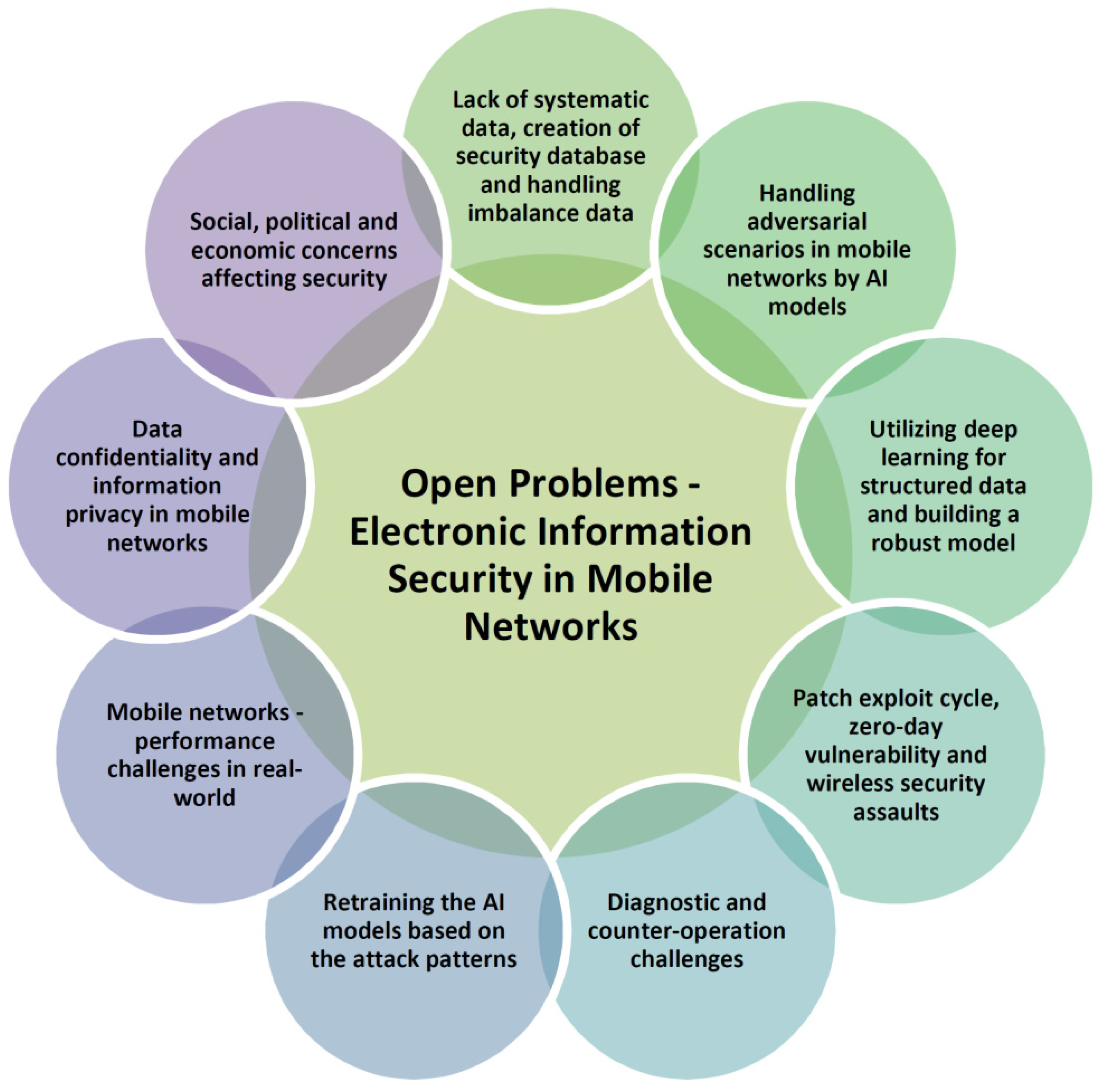
Sensors Free Full Text A Systematic Review On Machine Learning And Deep Learning Models For Electronic Information Security In Mobile Networks Html

Fema Test Answer Is 914 Surveillance Awareness What You Can Do Test Pinoy

Pdf Survey And Taxonomy Of Adversarial Reconnaissance Techniques

Information February 2022 Browse Articles

Pdf Survey And Taxonomy Of Adversarial Reconnaissance Techniques



No comments for "Adversarial Surveillance Is Conducted to Gather Information in Order to"
Post a Comment